What's new in Salt 3005 Phosphorus
24 minute read Updated:

It’s been 10 months and 2 CVE releases since the last major Salt version. If you do not have time to dig into all the cool stuff that went in, just read the first section about onedir packages because they will affect you sooner or later. For a shorter summary, check out the official announcement.
What's new in Salt 3005 Phosphorus: Onedir (Tiamat) packages, New SEPs, Internal refactorings, RESTCONF Proxy, Clouds, Ansible improvements, Nifty tricks.
- Onedir packages
- New SEPs
- Environments
- Salt SSH
- Internal refactorings
- Memory leaks
- Windows
- Pillar
- Proxy minions
- Clouds
- Operating systems
- Ansible improvements
- Nifty tricks
- Other notable features
Want to read about the upcoming Argon release?
I’m always hesitant to commit to writing another post like this one (it takes a lot of time!). However, I get bits of motivation to do so when people subscribe to the mailing list.
Powered by Mailgit
Onedir packages
Salt 3005 Phosphorus starts to use a new packaging tool called Tiamat that produces self-contained (onedir) packages. I’m not going to repeat the official guides that explain it in details. Instead I’ll try to highlight several important things and describe a bit how it works under the hood.
- Any new operating systems added in 3005 (like Ubuntu 22.04 or CentOS Stream 9) will only have onedir packages (see Platform package support for Salt 3005)
- The old Salt package builds for currently supported operating systems will be phased out by 3006 (see Timeline for upgrading to onedir packaging)
- The repository paths for classic and onedir packages are different
- The official announcement can be found at blogs.vmware.com
- Not sure if this is related, but VMware will open-source Native Minion and RaspberryPi packaging
- And apparently, SUSE is working on a similar packaging idea called Salt Bundle
Now to the technical details:
- The new packaging idea was proposed in SEP-26
- Tiamat uses PyInstaller under the hood
- The
onedirterm comes from PyInstaller’s--onedirflag, which creates an one-folder bundle (the other supported format is--onefileorsinglebinin Salt terms) - The other package format is called
singlebin, but it has some downsides. It was used by Heist (see my earlier “adventures” with it), but since then it also switched to onedir and now singlebin is only suitable for demo/lab purposes. - From an OS perspective it will look like a standard rpm/deb package, or a NSIS installer on Windows (no msi for now).
- Another packaging artifact is just a
tar.gzarchive (both foronedirandsinglebinvariants) that can be installed without any package manager. - The package includes a Python binary (currently 3.9.13 on Linux and 3.8.13 on Windows due to some deps being stuck on 3.8), Salt code, and all its dependencies like ZeroMQ (except libc). In other words, it is like a virtualenv + an isolated Python interpreter.
- Salt bootstrap script gained the new
onediroption to choose the corresponding package format - The package is installed into
/opt/saltstack/salt, but the standard/usr/bin/salt-*wrapper scripts are still there. On Windows that would be%PROGRAMFILES%/Salt Project/Saltby default, plus the usualsalt-*.batwrappers. - However, the process name has changed and looks like
/opt/saltstack/salt/run/run SUBCOMMAND(salt.exe SUBCOMMANDon Windows). Oh, and thesetproctitlelibrary is included, so we can have extended process names out of the box! - The complete list of subcommands is:
minion,master,call,api,cloud,cp,extend,key,proxy,pip,run,shell,spm,ssh,support,syndic,python. - Correspondingly, the
pythonexecutablegrain will return/opt/saltstack/salt/run/runon Linux andC:\Program Files\Salt Project\Salt\bin\salt.exeon Windows. But it is the Salt binary entry point, not a Python interpreter. Thepythonsubcommand was added to mitigate that. - Since it is a self-contained environment, we can expect more frequent security updates due to issues in any of the bundled dependencies. Because of that, I’m not sure we will ever see Salt onedir packages being included into a major Linux distro…
- Python libs that are installed using an OS package manager like
aptoryumwon’t be visible by Salt modules. For example, now Salt has to useaptCLI to manage Debian packages because the system-levelpython3-aptwasn’t functional - As a consequence, you have to use the new
salt-piputility to install Python dependencies into the onedir environment. The modules will be installed into/opt/saltstack/salt/pypath/on Linux (it is configurable via theTIAMAT_PIP_PYPATHenv var). On Windows, things are more complicated. I guess we can expect serious issues with binary modules and possible version conflicts. - A better and Windows-friendly method to install Python modules into an onedir environment is to use the
pip.installedstate. For onedir packages it will install stuff into the right location by default. However, if you used this state to install Python modules into other (system) locations (i.e. not for Salt), then you have to specifypip_binorbin_envarguments. - You might have to reinstall these dependencies for every Salt upgrade. As a minimum, you’ll need to do that when an upgrade brings a major Python version bump because the install path looks like
/opt/saltstack/salt/pypath/lib/pythonX.Y/site-packages/. In the worst case, you’ll need to upgrade them in place, because of possible version constraint clashes between modules in pypath and Salt deps in onedir. I expect the latter ones will change quite often because Salt has to have more frequent security updates for all this vendored stuff. - VMware plans to investigate automating a reinstallation when there is a new onedir upgrade, see the Q&A section
- The top-level repository for the onedir packaging toolchain is salt-pkg. Other parts of the puzzle are located in pkgr, tiamat, tiamat-pip, pyinstaller hooks, and run.py. You might need that if you decide to build custom onedir packages with patches or additional libraries.
New SEPs
These SEPs are not tied to the Salt Phosphorus release, but happened around the same time and are quite important.
- Extract Salt modules and convert most of them into external Salt Extension repositories
- LTS release strategy
- Deprecate and remove all usage of the
__utils__Salt loader
Environments
Saltenv support is somewhat convoluted and has many tricky corner cases. In theory, it could be solved by a proper abstraction layer, but it would be a huge undertaking. For now, it seems that a more pragmatic approach is to focus on the corner cases:
- State includes now work as expected for catch-all environments that are enabled by the
__env__keyword. PR #61201 by Nicholas Hughes - Add
__env__substitution inside file and pillar root paths. PR #61531 by Nicholas Hughes - Allow the
cpmodule functions to derivesaltenvfrom config if not explicitly set as a keyword argument to the function. PR #61564 by Nicholas Hughes - Use the actual Salt environment name for the file listing cache file on the master. This prevents incorrect file list information to be returned to minions using dynamic environments. PR #61739 by Nicholas Hughes
- Fix
cmdmodignoreingsaltenvset in configuration file. PR #61598 by Thomas Phipps - Fix
state.show_state_usagewhen using other than base environments (like when having SSE installed). PR #61648 by Michael Steed
Salt SSH
- A password for login to a system using
salt-sshcan now be used for sudo escalation. PR #61910 by Nicholas Hughes - The
sshmodule now accepts all ssh public key types as of OpenSSH server version 8.7. PR #60128 by Maximilian Eschenbacher - Fix
salt-ssherror when targeting IPs or hostnames directly. PR #60729 by @javicacheiro - Ensure
testis added to__opts__when states are run withsalt-sshPR #61634 by Megan Wilhite - Allow use of the
rosterarg insalt.functionstate when using SSH client. PR #58679 by Teddy Andrieux - Make it possible to pass extra parameters to salt-ssh pre-flight script with
ssh_pre_flight_argsfrom the roster. Apparently, this is used by Uyuni and SUSE Manager. PR #61715 by Victor Zhestkov
Internal refactorings
- Refactor transports to make them more pluggable (as I noted earlier, the likely goal is to integrate with the VMware’s RabbitMQ offering). This PR adds the concept of channels, that handle specifics related to salt such as message structure, authentication, etc. Transports are simplified to only handle sending and receiving messages over the wire PR #61450 by Daniel Wozniak
- Remove
SaltMessageServer.shutdownandLoadBalancerWorker.stopin tcp transport. PR #61703 by Megan Wilhite - Enable minion’s IPC channel to aggregate results from spawned jobber processes. Use a long-running request channel in the minion parent process to communicate job results back to the master via broker-based or broker-less transport. This is a necessary optimization at scale for transports that prefer a sustained long-running connection because connection create/dispose operations are expensive. The working assumption is that this change benefits all supported transports. PR #61468 by @devkits
- Support loading grains functions with Python type annotations. PR #60285 by Benjamin Drung
- Make
sys.argspechandle functions with Python type annotations. PR #61080 by Michael Steed - Don’t leak sub-processes in the
hgfsfileserver backend. PR #61684 by Pedro Algarvio - Fix ThreadPool leak in fqdn lookup. PR #61777 by Wayne Werner
- The
ProcessManagernow starts instances of the customProcessclass. PR #61603 by Pedro Algarvio - Multiprocessing logging no longer uses multiprocessing queues which penalized performance. Instead, each new process configures the terminal and file logging, and also any external logging handlers configured. PRs #61629 and #62013 by Pedro Algarvio
- Enforce config types (e.g. to prevent strings from being interpreted as lists and end up with something like [’s’, ’t’, ‘r’, ‘i’, ‘n’, ‘g’]). PR #61852 by Shane Lee
- Automate release tag, changelog, and man pages with Github Actions. PRs #61031 and #62099 by Megan Wilhite
- Add support for etcd v3 (v2 is still available if you set
etcd.require_v2: true). The support is enabled for execution, state, pillar, returner, and sdb modules, but not for the etcd cache module. PR #61911 and #62160 by Caleb Beard - Change the way the transactional-update module is working internally in order to run Salt actions inside of transactions (supported on MicroOS that provides a read-only rootfs and a tool, transactional-update, that takes care of the management of the system in an atomic way). Instead of using the SSH wrappers, Salt thin and
state.pkgin order to execute a Salt action inside a transaction, the module now uses a normalsalt-callexecution with the newconcurrent=trueoption forstate.applyand--no-return-eventoption forsalt-call. PR #61188 by Pablo Suárez Hernández - All of Salt’s loaders now accept
loaded_base_nameand only functions defined on the modules being loaded will be added to the lazy loader. PRs #62189 and #62250 by Pedro Algarvio
Memory leaks
A couple of non-obvious memory leaks were fixed, and it resulted in a much more predictable Salt Master memory consumption:
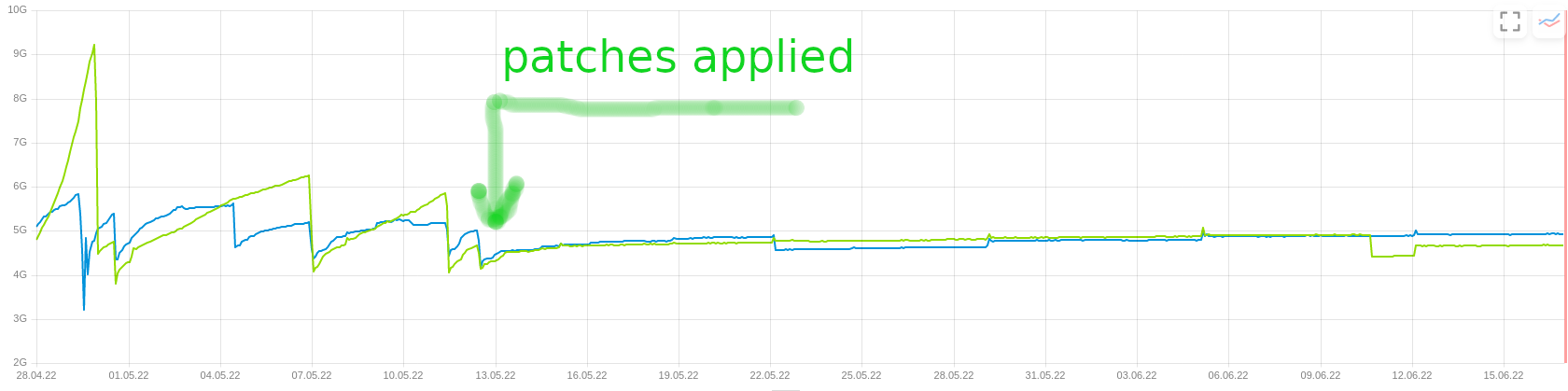
Image by Sergey Kacheev
- Fix memory leak in
modules/lxd.py. PR #62006 by Sergey Kacheev - Fix memory leak in
utils/jinja.py. PR #62007 by Sergey Kacheev - Fix
yamlloader.DuplicateKeyWarningleaking. PR #62021 by Sergey Kacheev
These fixes resulted in SEP-65 (also see #62191), which proposes deprecating the __utils__ dunder.
Windows
- Use
netinstead ofscto restart the salt-minion service on Windows. Thenetcommand will not return until it completes, whereas thesccommand just fires the stop or start and returns. Usingnetavoids this race condition and removes the need for the sleep command. PR #61383 by Shane Lee - Add the
forceoption tofile.symlinkto overwrite an existing symlink with the same name. Usesalt.utils.path.readlinkto handle junctions on Windows. PR #61326 by Shane Lee - Allow symlink to be created if the source is missing on Windows. PR #61545 by Shane Lee
- LGPO: Fix the ability to modify the “Audit: Force audit policy subcategory settings…” policy; search for policies in a case-sensitive manner first, then fall back to case-insensitive names. PR #61528 by Shane Lee
- Removed support for old-style Windows Group Policy names. Recommended policy names will be displayed in the comments. PR #61712 by Shane Lee
- Make
wuastates to return all changes, failures, and supersedences (instead of only returning a single item changed or failed). PR #61710 by Shane Lee - Make the salt.utils.win_dacl.get_name() function include the “NT Security” prefix for Virtual Accounts. Virtual Accounts can only be added with a fully qualified name. PR #61272 by Shane Lee
- Display packages marked
NoRemoveinpkg.list_pkgsso that they can be managed with Salt. They can be updated, but not removed. PR #61908 by Shane Lee - Re-enable tiamat-pip on Windows. PR #61586 by Pedro Algarvio
- Ability to get file version information on Windows. The
file.versionfunction will get just the version;file.version_detailswill get additional information. Not all files have version information. The common file types that contain version information are.exe,.dll,.sys. PR #62054 by Shane Lee @amalaguti - Add
win_shortcutexecution and state modules for working with.lnkfile shortcuts on Windows. Also split out thefile.shortcutcode into its ownshortcutexecution module and state module. Deprecate thefile.shortcutstate function in Salt 3008 Argon. PR #62025 by Shane Lee
Pillar
- Clear and update the pillar cache when running
saltutil.refresh_pillar. This only affects users that havepillar_cacheset to True. If you do not want to clear the cache you can pass theclean_cache=Falsekwarg tosaltutil.refresh_pillar. PR #60975 by Megan Wilhite - Support querying for JSON data in external SQL pillar. If you specify
as_json: Truein the mapping expression and query only for a single value, returned data are considered in JSON format and will be merged directly. PR #59777 by Ondřej Holeček - Fix
pillar_roots.writeon pillar subdirs. PR #59944 by Florin Stancu
Proxy minions
A couple of fixes to stabilize the DeltaProxy code:
- Handle the situation where the control proxy is configured to control a proxy minion whose pillar data could not be loaded. PR #61251 by Gareth J. Greenaway
- Don’t block minion startup when controlled proxy minions fail. PR #61665 by Gareth J. Greenaway
- Ensure config module loads opts from the loader context. This fixes proxy minion configuration handling. PR #61732 by Gareth J. Greenaway
Restconf proxy
The restconf modules (execution, state, proxy) are based on the RESTCONF protocol and can be used to manage network devices like Cisco, Juniper, Huawei, etc. that support it. The proxy module requires device credentials to be defined in a pillar.
Available execution module functions:
infoget_dataset_datapath_check
Available state module functions:
config_manage
PR #58965 by Jamie (Bear) Murphy
Clouds
- Deprecate all Azure cloud modules (will be removed in Salt 3007). The old “Classic” API is going away in March 2023, and the Resource Manager modules are moving to a Salt Extension. PR #62184 by Nicholas Hughes
- Support VMware instant clone feature. It is used to create powered-on virtual machines from the running state of another powered-on virtual machine. Instant cloning operations are not supported on standalone ESXi hosts, a vCenter server is required. PR #60004 by Anant Chopra
- Add support for CPU hot add/remove, memory hot add, and nested virtualization to VMware salt-cloud driver. PR #60739 by Gary T. Giesen
- Add
canonical_hosted_zone_name,canonical_hosted_zone_name_id, andvpc_idtoboto_elb.get_elb_configreturn data. The functionality is needed to be able to determine the hosted zone id to automatically create ALIAS Route53 records for new classic ELBs. PR #52774 by Anita Krueger - Fix
boto3_route53module for Python 3. PR #60951 by Indra Gunawan - Add
metadata_gcegrain to handle the new style GCE metadata server (which is not EC2-compatible). PR #61190 by Thomas Phipps - Load the Hetzner Cloud module configuration from the following sources (in order): VM configuration, VM profile configuration, VM provider configuration, Salt Cloud configuration if global searching is enabled, a provided default. PR #61400 by Henrik Hüttemann
- Make Hetzner Cloud
show_instancefunction an action. PR #61394 by @fkantelberg - Set the
virtualgrain on FreeBSD EC2 instances running on AWS Nitro hypervisor. PR #61169 by @amendlik - Add the ability to request VPC peering connections in different AWS regions (
boto_vpc). PR #54652 by Gareth J. Greenaway - Determine IP address from QEMU agent. To use this option, set
agent_get_ipin the cloud profile to1(integer). When the VM boots and the agent is started it will fetch the IP address of the QEMU VM and use that IP for the next actions in Salt Cloud. PR #61146 by Sander Cornelissen
Operating systems
- Remove Fedora 34 (EoL). PR #62076 by Kirill Ponomarev
- Add Fedora 35 to CI runs. PRs #61228 by Bryce Larson and #61942 by Kirill Ponomarev
- Remove EOL CentOS 8 from CI. PR #61408 by Kirill Ponomarev
- Add CentOS Stream 9 to CI. PR #62090 by Caleb Beard and #62193 by Kirill Ponomarev
- Various changes and fixes that are needed to add PhotonOS into CI. Photon OS is an open-source minimalist Linux operating system from VMware that is optimized for cloud computing platforms, VMware vSphere deployments, and applications native to the cloud. PR #61518 by Gareth J. Greenaway , #61677 by Pedro Algarvio
- Remove support for macOS Mojave. PR #61130 by Bryce Larson
- Update the welcome and conclusion pages of the macOS installer, add docs. PR #61437 by Shane Lee
- Implement YUM and DNF support on AIX. PR #61361 by David Murphy
- Add FreeBSD 13.1. PR #62068 by Kirill Ponomarev
- Prepare the test suite for Ubuntu 22.04. PR #62073 by Caleb Beard
- Add Ubuntu 22.04. PR #62100 by Kirill Ponomarev
- Support macOS defaulting to spawn as the default multiprocessing method. PR #57028 by Pedro Algarvio
- Add
suse_ipmodule allowing to manage network interfaces (throughnetwork.managed) on SUSE-based Linux systems. PR #60702 by Victor Zhestkov
Ansible improvements
A couple of improvements in the ansible module that allows running Ansible playbooks via Salt:
ansible.targets- return Ansible inventory from a specified inventory fileansible.discover_playbooks- discover Ansible playbooks stored under the given path or from multiple paths- Allow new types of targets (e.g. list) for the Ansible roster
- Do not consider “skipped” targets as failed for
ansible.playbooksstates
PRs #60056 and #60983 by Pablo Suárez Hernández
Nifty tricks
Autodetect module.run syntax
The use_superseded: [module.run] option is no longer needed (and taken into account) - you can mix and match both styles in a single state or orchestration file:
old_style_echo:
module.run:
- name: test.echo
- text: Hello there!
new_style_echo:
module.run:
- test.echo:
- Hello there!
old_style_arg:
module.run:
- name: test.arg
- args:
- arg1
- arg2
- kwargs:
kw1: kwarg1
kw2: kwarg2
new_style_arg:
module.run:
- test.arg:
- arg1
- arg2
- kw1: kwarg1
- kw2: kwarg2# salt-call state.apply module_run_example
local:
----------
ID: old_style_echo
Function: module.run
Name: test.echo
Result: True
Comment: Module function test.echo executed
Started: 06:14:05.062176
Duration: 3.677 ms
Changes:
----------
ret:
Hello there!
----------
ID: new_style_echo
Function: module.run
Result: True
Comment: test.echo: Hello there!
Started: 06:14:05.066995
Duration: 2.261 ms
Changes:
----------
test.echo:
Hello there!
----------
ID: old_style_arg
Function: module.run
Name: test.arg
Result: True
Comment: Module function test.arg executed
Started: 06:14:05.069479
Duration: 2.073 ms
Changes:
----------
ret:
----------
args:
- arg1
- arg2
kwargs:
----------
kw1:
kwarg1
kw2:
kwarg2
----------
ID: new_style_arg
Function: module.run
Result: True
Comment: test.arg: Success
Started: 06:14:05.071975
Duration: 2.2 ms
Changes:
----------
test.arg:
----------
args:
- arg1
- arg2
kwargs:
----------
kw1:
kwarg1
kw2:
kwarg2
Summary for local
------------
Succeeded: 4 (changed=4)
Failed: 0
------------
Total states run: 4
Total run time: 10.211 msWith that said, I recommend always using the new syntax. Having a CI check that is triggered by the old syntax will help transition to the new one. But because salt-lint does not have a such check, you can use the following command (e.g. with a highstate):
salt-call state.apply module_run_example test=true -l debug 2>&1 | grep 'legacy module.run syntax'
[DEBUG ] Detected legacy module.run syntax: old_style_echo
[DEBUG ] Detected legacy module.run syntax: old_style_argPR #61772 by Daniel Wozniak
Success/failure percentages
When the master/minion state_output_pct option is set to true, a summary will show successful and failed operations in a state run as a percentage of total operations:
Summary for local
------------
Succeeded: 4 (changed=4)
Failed: 0
Success %: 100.0
Failure %: 0.0
------------
Total states run: 4
Total run time: 4.275 ms
PR #60991 by Nicholas Hughes
Roll-up duplicate state IDs
The state_compress_ids master/minion option will roll an output of the following state block into two sections instead of four (esp. useful with state_output: terse_id):
mix-matched results:
cmd.run:
- names:
- "true"
- "false"
- "/bin/true"
- "/bin/false"Before:
salt-call state.apply phosphorus.rollup -l critical
local:
Name: mix-matched results - Function: cmd.run - Result: Changed Started: - 05:58:23.470018 Duration: 5.567 ms
Name: mix-matched results - Function: cmd.run - Result: Failed Started: - 05:58:23.475857 Duration: 5.276 ms
Name: mix-matched results - Function: cmd.run - Result: Changed Started: - 05:58:23.481379 Duration: 5.02 ms
Name: mix-matched results - Function: cmd.run - Result: Failed Started: - 05:58:23.486660 Duration: 5.434 ms
Summary for local
------------
Succeeded: 2 (changed=4)
Failed: 2
Success %: 50.0
Failure %: 50.0
------------
Total states run: 4
Total run time: 21.297 msAfter:
salt-call state.apply phosphorus.rollup -l critical
local:
Name: mix-matched results (2) - Function: cmd.run - Result: Changed Started: - 05:59:26.910423 Duration: 11.555 ms
Name: mix-matched results (2) - Function: cmd.run - Result: Failed Started: - 05:59:26.916231 Duration: 12.202 ms
Summary for local
------------
Succeeded: 2 (changed=4)
Failed: 2
Success %: 50.0
Failure %: 50.0
------------
Total states run: 4
Total run time: 23.757 msWhen enabled, this option consolidates the state data by ID and result (e.g. success or failure). The earliest start time is chosen for display, duration is aggregated, and the total number of names is shown in parentheses to the right of the ID.
PR #61550 by Nicholas Hughes
Etag support
Several HTTP-capable file functions in Salt (file.managed, archive.extracted, etc) can generate unnecessary traffic by downloading files each time a state is applied. A couple of proposals were discussed in the past, see #38971, #43518, #45314, and #47962.
One of the standard methods to avoid that is to use server-side change detection based on Etag. This HTTP response header is an identifier for a specific version of a resource. It lets caches be more efficient and save bandwidth, as a web server does not need to resend a full response if the content was not changed.
This is exactly what was implemented:
- Add Etag support for file.managed web sources. PR #61391 by Nicholas Hughes
- Remove case sensitivity of Etag header for
use_etag. PR #61441 by Nicholas Hughes - Add Etag support to archive.extracted. PR #61764 by Nicholas Hughes
Refer to your web-server docs on how to enable Etag support if it is not enabled by default.
New Jinja filters
A couple of new Jinja filters, mostly from itertools:
combinationscombinations_with_replacementcompresspermutationsproductzipzip_longestdict_to_sls_yaml_params- turn a dictionary into a list of single-key dictionaries (Salt state parameters)flatten- flatten a list (optional parameters arelevelsandpreserve_nulls)human_to_bytes- given a human-readable byte string (e.g. 2G, 30MB, 64KiB), return the number of bytesrandom_samplerandom_shuffle
I wish Jinja had list comprehensions…
PRs #61503, #61833, #62227, and #62373 by Nicholas Hughes
Modify schedules while minion is not running
Implement the ability to add, delete, purge, and modify Salt scheduler jobs when the Salt minion (event bus) is not running. Now you can use salt-call --local schedule.add ... to modify the /etc/salt/minion.d/_schedule.conf.
PR #61423 by Gareth J. Greenaway
freezer.compare function
The freezer module was introduced in Salt 3000 Neon and can freeze and restore package sets. The new freezer.compare function will display the difference between two frozen states. The results are shown as a dictionary with keys for packages and repositories. Each key may contain a changes dictionary showing items that differ between the two frozen states. Items shown in the “old” changes but not the “new” were removed. Items in “new” but not “old” were added. Items shown in both probably updated/changed versions between freezes.
Here is a little demo:
salt-call freezer.freeze old
local:
True
apt install cowsay
salt-call freezer.freeze new
local:
True
salt-call freezer.compare old new
local:
----------
pkgs:
----------
new:
----------
cowsay:
3.03+dfsg2-7
repos:
----------PR #61682 by Nicholas Hughes
grains_refresh_pre_exec
Environments using dynamic grains from external sources often have a need to populate grains information in another tool (such as a DCIM) and have those grains immediately take effect during the next execution on a minion. With the current workflow, grains can only be refreshed manually, on an interval (causing potentially unnecessary polling), or after a highstate (when we wanted the grains refreshed before the highstate).
The grains_refresh_pre_exec setting (False by default) allows for a minion to check its grains prior to the execution of any operation to see if they have changed and, if so, to inform the master of the new grains.
PR #61709 by Nicholas Hughes
Jinja error context
Ever seen the dreaded jinja2.exceptions.UndefinedError: 'dict object' has no attribute 'foo' while being unable to find what particular dict object caused the error? Now it will be obvious:
local:
Data failed to compile:
----------
Rendering SLS 'base:phosphorus.foo' failed: Jinja variable 'dict object' has no attribute 'foo'; line 6
---
{% set myobj = {'baz': 'qux'} %}
foo:
test.configurable_test_state:
- changes: True
- comment: {{ myobj['foo'] }} <======================
---PR #61553 by Justin Findlay
YAML linting
A simple module based on yamllint to validate Salt state files. Here is an example:
foo:
test.configurable_test_state:
- changes: True
- comment: A commentpip install yamllint
salt-call yaml.lint salt://phosphorus/foo.sls
local:
----------
problems:
|_
----------
column:
6
comment:
wrong indentation: expected 4 but found 5 (indentation)
level:
warning
line:
3
|_
----------
column:
5
comment:
syntax error: expected <block end>, but found '<block sequence start>' (syntax)
level:
error
line:
4
source:
foo:
test.configurable_test_state:
- changes: True
- comment: A commentBy default, it expects a plain yaml file, but can optionally pass the file through a renderer system if you specify the pre_render=jinja argument. The linter config is hardcoded and reflects the Salt yaml style as close as possible. In future versions, it might be extended to support custom yamllint configs as well.
PRs #61183 and #62243 by Thomas Phipps
Dpkg notify plugin
This is a dpkg plugin developed by SUSE to send notifications when new packages are installed outside of Salt. It complements the existing yumnotify and zyppernotify plugins, plus an upcoming dnfnotify plugin.
It is not a part of the Salt package, so to use it:
- Install as described in the README
- Grab the
pkgsetbeacon from Uyuni Project, put it into the_beaconsdir then runsalt-call saltutil.sync_beacons - Add the following snippet to the minion config (or minion’s pillar) and restart the minion
beacons:
pkgset:
- interval: 5Then, when you install or remove any package manually (using apt-get), the minion will emit an event like this:
salt/beacon/minion/pkgset/changed {
"_stamp": "2022-07-18T08:20:38.979858",
"id": "minion"
}There is no information in the event that mentions what package was installed. To determine that you can use the pkg.list_pkgs function or the freezer module.
PR #61180 by Victor Zhestkov
Other notable features
- Add
pkg.heldandpkg.unheldstate functions for Zypper, YUM/DNF and APT. Allowzypperpkg.holdandzypperpkg.unholdfunctions to operate on a different root directory. PR #60432 by Victor Zhestkov - Consul state module with
acl_presentandacl_absentfunctions. PR #58101 by @remijouannet and Gareth J. Greenaway - New
gpg_decrypt_must_succeedmaster/minion option (Falseby default) to have GPG decrypt failures treated as errors. PR #61418 by Justin Findlay - Event return capability in Splunk returner. PR #61150 by @mymindstorm
- Introduce the ability for the Tiamat-built Salt binary to install/use pip-installed modules from a configurable location (defined by the
TIAMAT_PIP_PYPATHenvironment variable). PR #61938 by Nicholas Hughes - Set default transport and port settings for Napalm NXOS, if not set. PR #61556 by David Murphy
- Deprecate and remove
salt-unity. PR #61287 by Gareth J. Greenaway - Handle new MariaDB SLAVE MONITOR grant. PR #61382 by Sebastien BLAISOT
- Handle Ctrl-C gracefully. PR #61363 by Caleb Beard
- Don’t output
salt.functionorchestration return recursively in highstate outputter. PR #61583 by Caleb Beard - Add
--allow-downgrades(via theallow_downgradesoption) capability forapt.upgrade. PR #61469 by @jakelyz - Remove the
grains.get_or_set_hashfunction. Please reference pillar and SDB documentation for secure ways to manage sensitive information. Grains are an insecure way to store secrets. PR #61702 by Megan Wilhite - Remove the
telnet_port,serial_type, andconsoleparameters insalt/modules/virt.py. Use theserialsandconsolesparameters instead. PR #61705 by Megan Wilhite - In large environments with 1000s of minions, some commands were causing tracebacks due to the
retkey not being found in the data dictionary when processing job responses. This change correctly handles failed returns from jobs sent in batch mode. PR #61728 by David Murphy - Convert relative paths to absolute as their associated sls file is processed. This fixes conflicting state IDs for relative and absolute includes being used simultaneously. PR #61659 by David Murphy
- Fix bytes vs text encoding issue for sqlite SDB. PR #61794 by Wayne Werner
- Fix
salt-call event.sendcall with grains and pillar. PR #61256 by Cedric Bosdonnat - Allow for additional options for xmit hash policy in mode 4 NIC bonding on RedHat / Centos. PR #61668 by David Murphy
- Speed up the
zfs.filesystem_presentandzfs.volume_presentstates. PR #59970 by Alan Somers - Add
dig.cnamefunction. PR #61992 by Nicholas Hughes - Tons of Zabbix module issues and compatibility fixes. PR #62012 by Jerzy Drozdz
- When states are running in parallel, ensure that the total run time produced by the highstate outputter takes that into account. PR #62000 by Gareth J. Greenaway
- Add
retryfunctionality whenparallelis set toTrue. PR #61631 by Gareth J. Greenaway - Fix
items,values, andkeysfunctions in the data module. PR #62024 by Gareth J. Greenaway - Update
states.cheffor version 16.x and 17.x Chef Infra Client output. PR #61893 by @ericham - Allow the
emitatstartupbeacon option to work when thedelayoption is set. PR #62096 by Gareth J. Greenaway - Better search for
useradd,usermod, anduserdelcommand paths. PR #62088 by Nicholas Hughes - Properly handle
test=truemode forfile.managedwithfollow_symlinks=true. PR #62067 by Petr Pavlu - Apt-key is on a deprecation path right now so with
aptkey=Falseit is now possible to usepkgrepo.managedwithoutapt-key. Also, change signedby default directory to/etc/apt/keyrings. PRs #61760, #62159 by Megan Wilhite and #62177 by Imran Iqbal - Extend
file.tidiedto include the following functionality: exclusion regular expressions, allow match and exclusion regular expressions to match on the whole path instead of just the file/directory name, follow symlinks, compare the change and modified times of the file to the current date instead of just access time. PR #61824 by Nicholas Hughes - Ability to ignore missing regex matches in a file when using the
file.commentstate. This allows for a “comment only if a match is found” workflow and prevents unnecessary state failures or requisite use. PRs #62045 and #62122 by Nicholas Hughes
You can find other changes and bugfixes in the official CHANGELOG.md and Release Notes
Want to read about the upcoming Argon release?
I’m always hesitant to commit to writing another post like this one (it takes a lot of time!). However, I get bits of motivation to do so when people subscribe to the mailing list.
Powered by Mailgit